Azure Authentication Methods Policy: What is it and what does it change?
If you've been looking around in the Azure portal, you may have seen a newer blade in the menu named Authentication Methods
If you've been looking around in the Azure portal, you may have seen a newer blade in the menu named 'Authentication Methods' under the Azure Active Directory Security hub. The Authentication Methods Policy is a newer feature in Azure that is optional now, but will become mandatory before you know it.
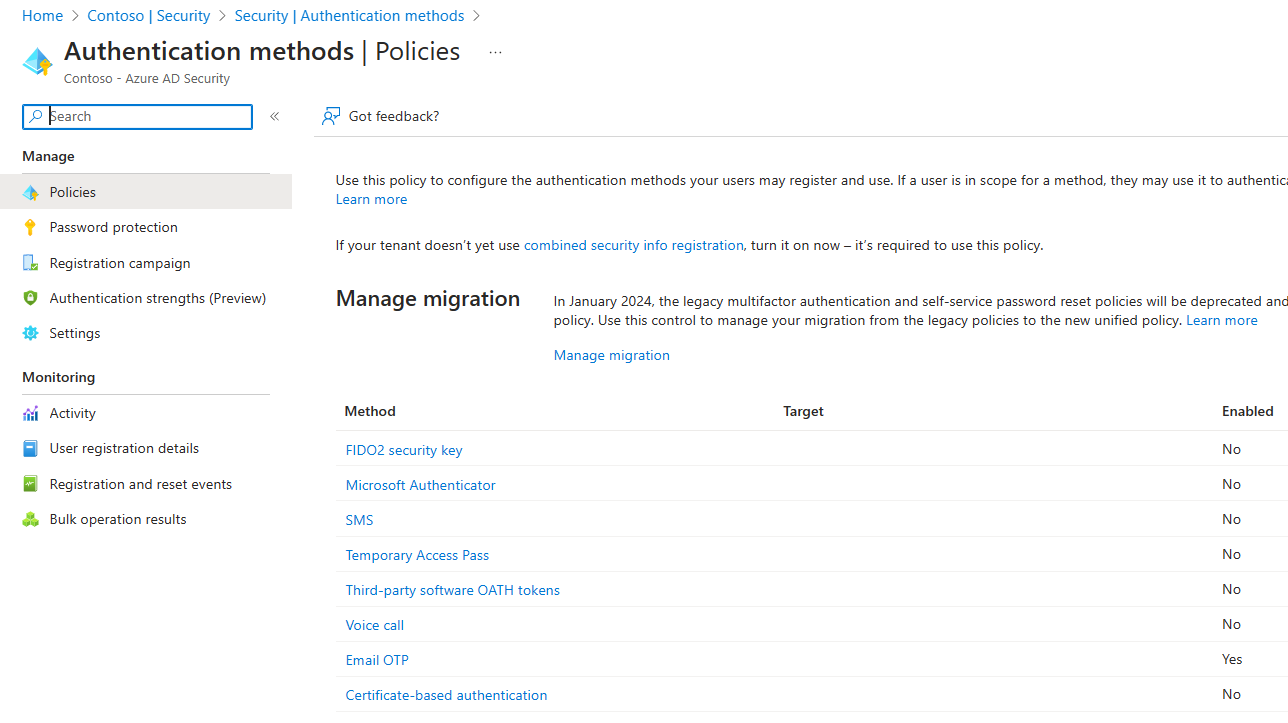
The Authentication Methods Policy is the first big push that Microsoft is doing towards deprecating the legacy cloud MFA method, Per-User MFA. Per-User MFA has been around as a default option to enforce and configure MFA on free Azure subscriptions for years, before many companies had even considered migrating their operations to the cloud. Over that time period, alternative methods for MFA like Conditional Access Policies and Security Defaults have come in and seen great usage, with Security Defaults now being enabled by default on all newly provisioned Azure tenants.
It's an open secret that Per-User MFA has been somewhat of a thorn in the side of Azure security for some time. The user interface for Per-User MFA exists outside of the normal Azure and M365 portals. Script management of Per-User MFA can only be done in PowerShell through the MSOnline module (which is being deprecated itself), and Per-User MFA has never been exposed through APIs like MS Graph or MS Defender that Microsoft is clearly putting a lot of resources into developing.
Per-User MFA can be thought of as having 2 key functions: user enforcement of MFA and approved MFA methods. The Authentication Methods Policy has been developed to replace the Per-User approved methods, so half of Per-User MFA. At time of writing, Microsoft has not announced plans to deprecate the enforcement capabilities of Per-User MFA.
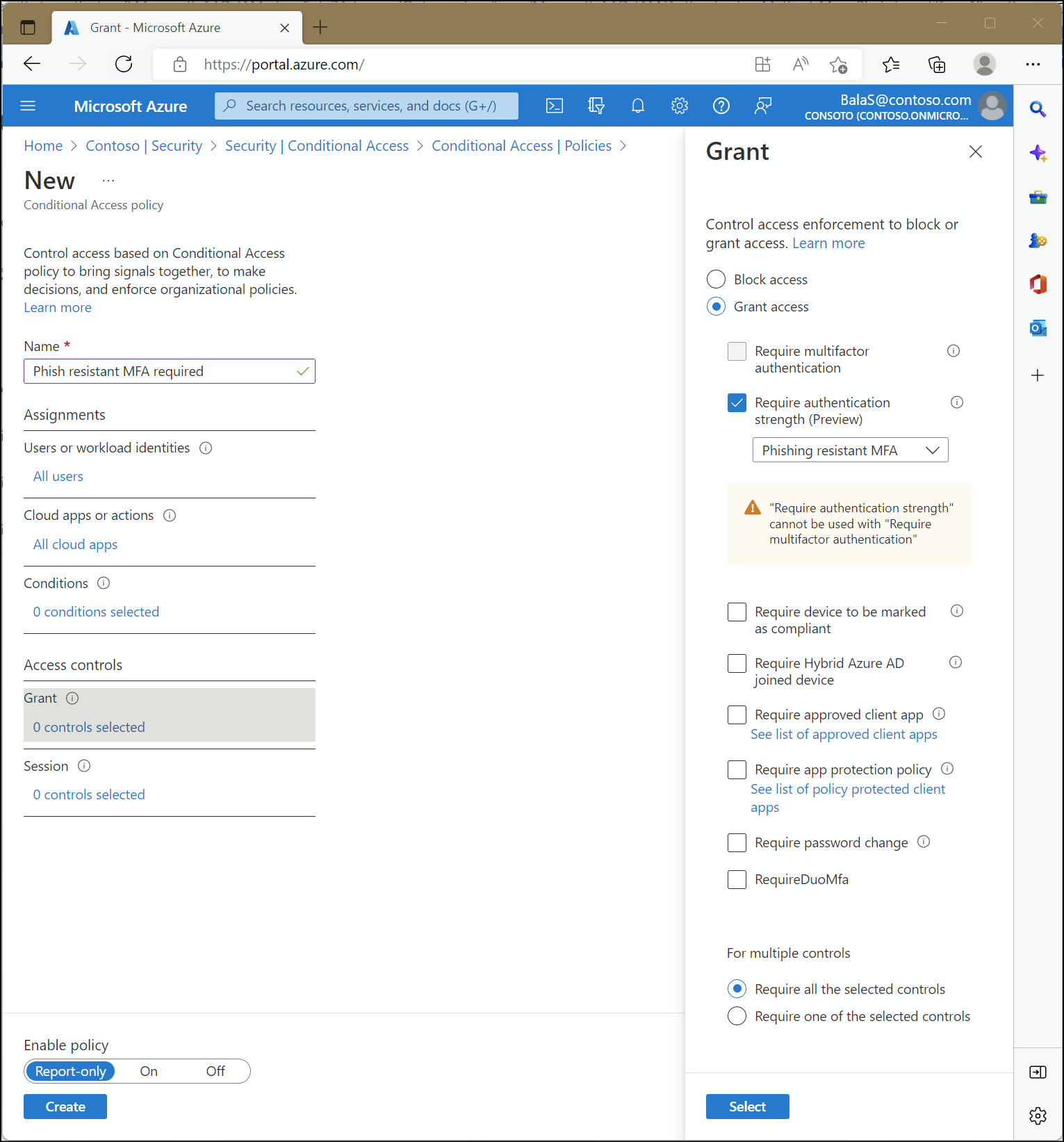
With the Authentication Methods Policy comes an upgrade to the capabilities in the form of System-Preferred MFA, where the organization can encourage users towards stronger MFA methods. Organizations are also able to define Authentication Strength lists of different MFA methods. These Authentication Strengths can then be used as another control in your Conditional Access Policies to require strong MFA methods for access to sensitive data and applications.
If you go to the Authentication Methods Policy page in Azure or M365, you will also see a notice that legacy MFA policies are being deprecated in September 2024, along with links to Microsoft documentation migration guides. These will tell you how both the Per-User MFA and Authentication Methods Policy will be respected during migration process.
The takeaway here is that Per-User MFA is slowly but surely being replaced in Azure by newer modern MFA administration tools. Microsoft have made the smart choice to give all customers a long runway until these new controls are in place, especially for larger organizations that need that runway to migrate smoothly. Change is coming, and Azure will be able to be more secure and better managed because of it.
Sources:
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods-manage
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-strengths
https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/azure-ad-change-management-simplified/ba-p/2967456