Senserva and Azure Active Directory Applications
Azure has a strong foundation that is built on Applications in Active Directory. Much of the functionality that is commonly seen and used in Microsoft's environment, such as Microsoft Outlook, Microsoft Teams, Microsoft Graph, and many more.
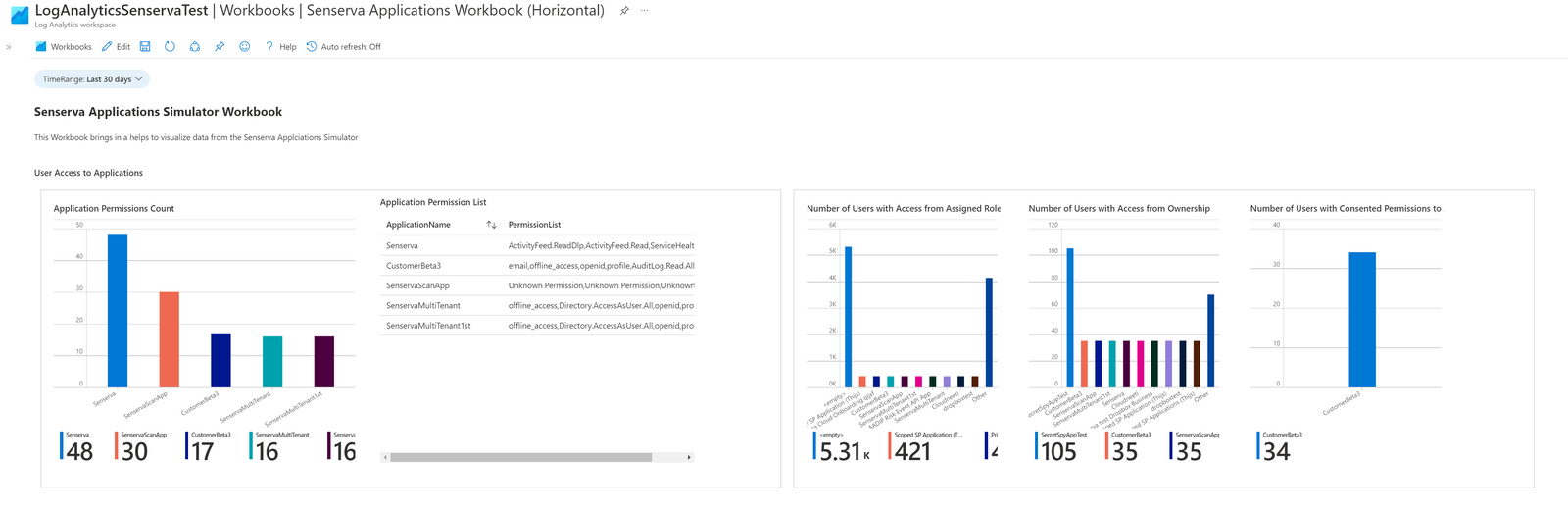
Azure has a strong foundation that is built on Applications in Active Directory. Much of the functionality that is commonly seen and used in Microsoft's environment, such as Microsoft Outlook, Microsoft Teams, Microsoft Graph, and many more are Applications that are granted permission to the tenant.
These Active Directory Applications help to reduce some of the friction of the cloud, by having a central instance of an Application with needed functionality and with several Active Directory User Accounts who get permission to use the Application. The security issues arise when scope creep occurs, Applications with excessive permission and User Accounts with excessive access. Security concerns also come about from Applications with insecure configurations.
The patented Senserva Bot has been built with the Application Simulator, to review your Applications for both User access and configuration review. User access can be dictated directly through Ownership, or indirectly through Active Directory Role Assignment. Legacy configurations like TLS 1.0 and Implicit Grants are still available but are not appropriate for the landscape of today. The Applications Simulator brings in all this data and more to provide analytics to you, automating review and protecting from breaches.